Insider Threats in Office 365 A Practical Guide for IT Admins
What are insider threats?
Insider threats are risks caused by people who already have legitimate access to your systems and data, employees, contractors, partners, volunteers, or students. They also include compromised insiders, where an attacker abuses a real user’s account. Motives range from mistakes and convenience through to financial gain, coercion, grievance, or curiosity.
Never miss an article and subscribe , and don’t forget to check out my YouTube channel

1) Accidental insiders
Well-intentioned users who cause harm by mistake.
Typical behaviours
- Sending a spreadsheet with personal data to the wrong external contact from Exchange Online.
- Creating an “Anyone with the link” share on SharePoint/OneDrive and pasting it into a public Team or email.
- Syncing a confidential library to a home PC with OneDrive, which a family member then accesses.
- Pasting sensitive text into a Teams chat with external guests, thinking it’s a private thread.
- Auto-saving a Word document with student or customer details into a personal Desktop folder that backs up to a private cloud.
Data exposure, breach notifications, regulatory reporting, and reputational damage.
2) Negligent insiders
Users who knowingly bypass policy for convenience, without intent to harm.
Typical behaviours
- Setting a mailbox auto-forward to a personal email address “to work from home more easily”..
- Using an unmanaged device to download files that policy says must stay on compliant devices.
- Building a Power Automate flow that emails reports (with personal data) to external recipients.
- Approving unexpected MFA prompts to “get back to work”.
Impact: silent data seepage and a culture of exceptions that normalises risky behaviour.
3) Malicious insiders
Users who intend to cause harm or profit.
Typical behaviours
- Selling access (credentials, session cookies, or app secrets) on criminal marketplaces or dark-web forums, or offering to run eDiscovery exports for a fee.
- Quietly creating inbox rules to hide replies while exfiltrating email to an external account.
- Registering a rogue Entra ID enterprise app with consent to high-privilege Graph scopes, then granting it tenant-wide access.
- Mass-downloading files from SharePoint/OneDrive and copying to personal cloud or removable media.
- Disabling Defender protections, altering audit settings, or adding back-door admin roles for later use.
data theft, extortion, sabotage, financial loss, and legal consequences.
4) Compromised insiders (account takeover)
A legitimate account is abused by an external attacker.
Typical behaviours
- Phishing or MFA fatigue leads to a hijacked account that creates forwarding rules, spins up OAuth apps, or invites external guests to Teams/SharePoint.
- Impossible travel or unusual IPs followed by mass file access.
- Token theft on an unmanaged device; the attacker reuses the session to download data without a password prompt.
Looks like normal user activity, so it blends in and is harder to spot.
Early warning signs across Microsoft 365
- Spikes in file downloads, deletions, or sharing link creation.
- New mailbox rules, especially “forward externally” or “move to RSS/Archive”.
- New high-privilege app consents (e.g.,
Mail.ReadWrite,Files.Read.All,Directory.ReadWrite.All). - Access from non-compliant devices, unusual countries, TOR/VPN exit nodes, or at odd hours.
- Users exporting PSTs or running eDiscovery outside normal roles.
- Creation of guest accounts or external Teams shares at odds with policy.
Office 365 is attractive to insiders because it combines email, files, and chats, and sharing is simple. The fix is layered: identity controls, data policies, activity monitoring, and clear processes.
Why Office 365 tenants are vulnerable?
- Broad access and sharing: collaboration is frictionless across Exchange, SharePoint, OneDrive and Teams; mistakes spread quickly.
- Trusted credentials: insiders sit past the perimeter; their actions often look legitimate.
- Remote access: home and mobile use opens the door to unmanaged devices if you don’t enforce compliance.
- Human error: small slip-ups (wrong link type, wrong recipient) can expose large datasets.
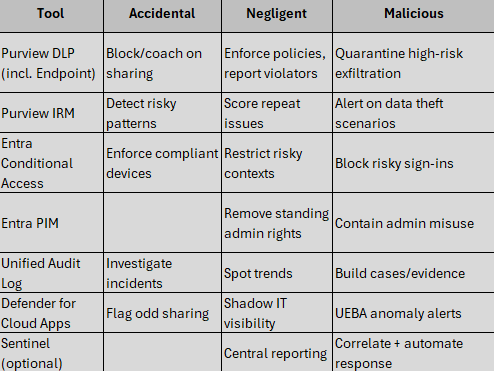
The Microsoft tools to use
- Microsoft Purview Insider Risk Management (IRM): correlates signals (audit logs, user activities, communications) to detect potential data theft, data leaks, or policy violations; triage alerts into cases with privacy controls.
- IRM policy templates: e.g., Departing users (catch mass downloads, forwarding rules, personal cloud copies near a resignation date) and Data leaks.
- Purview Data Loss Prevention (DLP) including Endpoint DLP: monitors and blocks oversharing of sensitive info across Exchange, SharePoint, OneDrive, Teams and on managed devices; policy tips coach users at the point of risk.
- Microsoft Entra ID (formerly Azure AD):
- Conditional Access and Identity Protection for risk-based MFA and sign-in risk policies.
- Privileged Identity Management (PIM) for just-in-time admin access, approval workflows and full audit.
- Access reviews to remove stale permissions and offboard quickly.
- Unified Audit Log: tenant-wide activity search and alerting for investigations.
- Defender for Cloud Apps: anomaly detections for unusual cloud usage and exfiltration patterns.
- Microsoft Sentinel: SIEM to correlate signals and automate responses at scale.
Deploy the basics
1) Insider Risk Management – start with “Departing users”
- Open Microsoft Purview portal > Insider risk management > Get started. Assign IRM roles to your analysts.
- Settings > connect the HR connector (resignation/termination dates) so policies can target leavers.
- Policies > Create policy > choose Data theft by departing users > scope to high-risk groups (sales, engineering, finance).
- Keep default indicators (mass downloads, printing, personal cloud copy, forwarding rules) and tune thresholds after a week of signal collection.
- Review Alerts daily; promote worthy alerts to Cases; use the user-activity timeline; keep users pseudonymised and only reveal when necessary.
2) Purview DLP – stop data walking out
- Purview portal > Data loss prevention > Policies > Create policy.
- Choose a template (e.g., Financial, Personal data) > locations: Exchange, SharePoint, OneDrive, Teams, and Devices for Endpoint DLP.
- Rules to start with:
- External email or link containing sensitive info > Block or Warn with justification.
- Copy to personal cloud/storage on devices > Block (Endpoint DLP).
- Add policy tips so users learn at the moment of risk.
- Review DLP reports weekly; refine rules and exceptions (service desks, trusted apps) to reduce noise.
3) Entra ID – keep access tight
- Conditional Access baseline:
- Require MFA for all users; block legacy auth.
- Apps with sensitive data (SharePoint/OneDrive, Exchange admin) > grant access only to compliant devices.
- Use Named locations and session controls to limit risky contexts.
- Identity Protection: enable user risk and sign-in risk policies; for Medium and above, require password reset/MFA. Check Risky users and Risky sign-ins reports.
- PIM for admins: Entra ID > Identity Governance > Privileged Identity Management > set admin roles to Eligible, require MFA/approval, time-bound activation, and enable access reviews and alerts.
4) Visibility – know what actually happened
- Unified Audit Log: Purview > Audit > Search; create saved queries for mass downloads, mailbox rule creation, permission changes, and file deletion spikes.
- Defender for Cloud Apps: connect Microsoft 365; review Anomaly detection alerts (impossible travel, activity spikes, unusual file sharing).
- Sentinel: connect Microsoft 365, Entra, Defender; enable analytics rules to auto-disable accounts or open tickets on correlated alerts.
Case study: Liver Shipping (business)
Context: International logistics firm handling client documents and route data across SharePoint, OneDrive and Exchange.
What they deployed
- IRM “Departing users” policy during a restructure; HR connector feeding resignation dates. Alerts on mass downloads and forwarding rules.
- DLP rules blocking external sharing of files tagged “Client Confidential”; Endpoint DLP preventing copy to personal cloud.
- PIM for Exchange/SharePoint admins; no standing global admins.
- Conditional Access enforcing compliant devices for SharePoint and OneDrive.
An alert flagged a departing salesperson uploading a client list to personal storage. DLP quarantined the file; the case was handled as a policy breach rather than a data leak. A separate IT admin attempt to bypass controls was contained because PIM denied actions without activation and approval.
Case study: Mill Town High School (education)
Context: Secondary school with A5 features for staff and students; sensitive pupil data in SharePoint/OneDrive; Teams used heavily.
What they deployed
- DLP with a Personal Data template to block emails or links containing student IDs outside the school domain; Endpoint DLP on staff laptops.
- IRM “Data leaks” policy for faculty to surface repeat risky sharing.
- Identity Protection risk policies and Conditional Access to require MFA and restrict access on unmanaged devices.
- Unified Audit Log saved searches for mailbox forwarding rules and bulk file downloads; regular access reviews to remove stale permissions.
Outcome: A mis-addressed spreadsheet was blocked by DLP; a risky sign-in was caught and remediated with a forced password reset. Off-boarding now disables accounts on the last working day.
Operating model and daily habits
- Least privilege always: use PIM, remove standing admin roles, run monthly access reviews.
- Build and tune policies: start broad, then narrow. Review IRM and DLP reports weekly; adjust thresholds and scopes.
- Watch the logs: treat the Unified Audit Log as your black box. Save queries; subscribe to alerts.
- Coach users at the edge: policy tips cut repeat offences without heavy-handed blocks.
- Offboard quickly: automate account disablement and file ownership transfer the day someone leaves; keep the IRM departing users policy permanent.
- Assume compromise: plan for account takeover; layer Conditional Access, Identity Protection and DLP to limit blast radius.
Insider threats are not a niche risk; they are part of everyday operations in Microsoft 365. The strongest position is a layered one: tight identity, guarded data, active monitoring, and clear processes that are rehearsed, not just written down. When you combine Entra ID controls, Purview policies, and disciplined offboarding, you cut both the likelihood and the impact of a mistake or a malicious act.
If you need a simple starting point, pick three actions and ship them this week:
- Enforce MFA with Conditional Access and put all admin roles behind PIM.
- Publish one high-value DLP policy (email and SharePoint/OneDrive) with policy tips.
- Enable a single Insider Risk policy for departing users and review alerts daily.
Next, schedule a short tabletop exercise for an insider incident, automate access reviews, and make weekly audit-log checks part of your routine. Treat every control as a living configuration: tune thresholds, shrink exceptions, and close the gaps you find.
Do the basics well, then iterate. With consistent habits and the tools you already own, insider threats become manageable, visible, and contained.
Feel free to buy me a coffee to keep this website up and running
What is an insider threat?
An insider threat is a risk caused by someone with legitimate access to your systems and data — such as employees, contractors, partners, volunteers, or students. It also includes compromised insiders, where an attacker abuses a real user’s account.
Why is Microsoft 365 vulnerable to insider threats?
Broad access across Exchange, SharePoint, OneDrive, and Teams
Trusted credentials bypass perimeter defences
Remote access from unmanaged devices
Human error and frictionless sharing
What are early warning signs?
Spikes in downloads or deletions
New mailbox rules (e.g. auto-forwarding)
High-privilege app consents
Access from unusual locations or devices
Guest account creation or external sharing
What’s the best operating model?
Least privilege: No standing admin roles
Policy tuning: Review IRM and DLP weekly
Routine monitoring: Audit logs and access reviews
User coaching: Use policy tips to guide behaviour
Fast offboarding: Disable accounts and transfer ownership immediatel
Check out this article
Tags: Cybersecurity, insider threats
[…] Check out this article Insider Threats in Office 365: A Practical Guide […]