Entra ID phishing-resistant MFA staged rollout with Authentication Strengths
Phishing keeps bypassing legacy MFA. Reverse-proxy kits intercept one-time codes and session cookies, allowing attackers to sidestep prompts entirely. Microsoft Entra ID’s phishing-resistant MFA blocks this by binding sign-in to a device-backed key, such as passkeys, FIDO2 security keys, or Windows Hello for Business and requiring real user presence. You can pilot it in Report-only mode, validate its impact through Conditional Access Insights, and enable it confidently. It’s one of the most effective controls that many organisations still haven’t implemented.
Entra ID phishing-resistant MFA lets you require methods that resist real-time phishing and token replay. This guide shows a safe rollout: enable passkeys/FIDO2 or Windows Hello for Business, pilot in Report-only, verify with Insights & Reporting and Sign-in logs, then enforce for admins and sensitive apps.
Never miss an article and subscribe, and don’t forget to check out my YouTube channel, Control Alt Delete Tech Bits

What counts as phishing-resistant in Entra ID?
The built-in Phishing-resistant MFA authentication strength accepts:
- FIDO2 security keys / passkeys
- Windows Hello for Business / platform credential
- Certificate-based authentication (multi-factor)
These methods resist real-time phishing and man-in-the-middle attacks.
Prerequisites
- Licensing: Microsoft Entra ID P1 for all users targeted by Conditional Access. Use P2 only if you will add risk-based policies/Identity Protection in the same rollout.
- Admin roles: An account with permission to manage Authentication methods and Conditional Access (e.g., Security Administrator or Conditional Access Administrator; Authentication Policy Administrator for method policies).
- Telemetry (recommended): A Log Analytics workspace. In Monitoring & health > Diagnostic settings, send SignInLogs and ConditionalAccess so the workbook has data.
- Devices & methods ready: Approved FIDO2 keys, WebAuthn-capable browsers, Windows Hello for Business on managed devices, and certificates if using CBA.
Rollout plan at a glance
- Set guard rails (break-glass, pilot groups).
- Enable phishing-resistant methods for the pilot.
- Create a Conditional Access policy that requires the Phishing-resistant MFA strength in Report-only.
- Monitor with Conditional Access – Insights & Reporting and Sign-in logs.
- Enforce for admins and critical apps, then expand.
Guard rails
Create pilot groups (Security groups)
- Path: Microsoft Entra admin centre > Microsoft Entra ID > Groups > All groups > New group
- Group type: Security
- Name: e.g.,
_PR-Pilot-Admins(repeat for_PR-Pilot-Usersif needed) - Create
- Open the group > Members > Add members > add your pilot users.

Create two emergency “break-glass” accounts and exclude them – Checkout this article about break-glass accounts
- Users: Microsoft Entra ID > Users > All users > New user (create two cloud-only accounts).
- Roles: Microsoft Entra ID > Roles & admins >Global Administrator > Add assignments > add both accounts.
- Exclusion group: Groups > New group > Security > name
_CA-Exclude-Emergency> Create > add both accounts as members. - You will exclude this group from every Conditional Access policy. Store credentials offline and test quarterly.
Enable phishing-resistant methods for the pilot
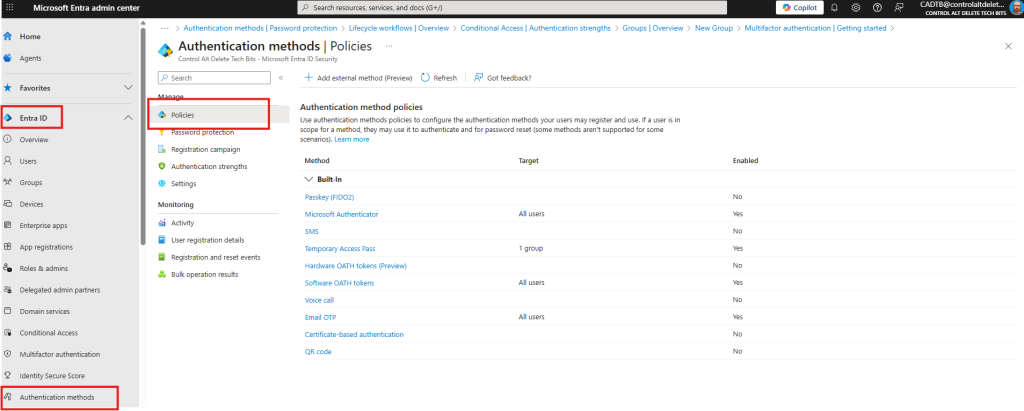
Menu names can appear under Protection or directly under Microsoft Entra ID, depending on your tenant. If you don’t see Protection, stay in Microsoft Entra ID and use the feature names below.
FIDO2 security keys / Passkeys
- Microsoft Entra ID > Authentication methods > Policies
- Click FIDO2 security key
- Enable: Yes
- Target: Include > Select groups > choose
PR-Pilot-Admins(and/or_PR-Pilot-Users) - Save
- If Passkeys is listed separately, repeat the same steps for Passkeys.
Windows Hello for Business (WHfB)
WHfB is a device configuration and a supported method; you enable the method policy in Entra and configure devices in Intune or via Group Policy.
- Enable the method policy in Entra:
- Path: Microsoft Entra ID > Authentication methods > Policies > Windows Hello for Business
- Enable: Yes > Target your pilot group > Save
- Configure devices (Intune example):
- Open Microsoft Intune admin centre > Devices > Windows > Windows Hello for Business (or Endpoint security > Account protection) → create and assign the WHfB policy to pilot devices.
Certificate-based authentication (CBA) (optional)
- Microsoft Entra ID > Authentication methods > Policies > Certificate-based authentication
- Configure issuer/trust as required > Enable: Yes > Target your pilot group > Save.
QR code authentication for frontline/shared devices
- Path: Microsoft Entra ID > Authentication methods > Policies > QR code
- Enable: Yes > Target your frontline group > Save.
Admin check for a user’s methods: Microsoft Entra ID > Users > select user > Authentication methods > confirm a passkey/FIDO2/WHfB or CBA is registered.
Create the Conditional Access policy (Report-only first)
- Path: Microsoft Entra ID > Conditional Access > Policies > New policy
- Name:
Require Phishing-Resistant MFA – Admin Portals (Pilot) - Assignments > Users: Include > Select groups >
_PR-Pilot-Admins(and/or_PR-Pilot-Users); Exclude > select_CA-Exclude-Emergency - Assignments > Target resources (Resources, formerly Cloud apps): Include > Select apps > choose Microsoft Admin Portals (or a small set of critical apps)
- Access controls > Grant: Grant access > Require authentication strength > select Phishing-resistant MFA > Select
- Enable policy: Report-only
- Create
Leave this in Report-only for a few days to measure impact before you enforce.
Monitor impact
Conditional Access – Insights & Reporting (policy-level view)
- Microsoft Entra ID > Monitoring & health > Workbooks > Conditional Access – Insights & Reporting
- At the top of the workbook:
- Policy: choose
Require Phishing-Resistant MFA – Admin Portals (Pilot) - Time range: set e.g., Last 7 days
- Policy: choose
- Review succeeded / would failed, user and app breakdowns, and reasons.
- If the workbook is empty: Monitoring & health > Diagnostic settings > ensure SignInLogs and ConditionalAccess are streaming to your Log Analytics workspace.
Sign-in logs
- Microsoft Entra ID > Monitoring & health > Sign-in logs
- Open a recent entry for a pilot user > Conditional Access tab
- Check Applied policies, Result, and the Authentication requirement. Use this for helpdesk triage.
Enforce, expand, and keep visibility
- Open your pilot policy: Conditional Access > Policies > select policy
> Enable policy: switch from Report-only to On > Save - Expand Assignments > Users to include all admins; monitor for a week
- Add more Target resources and user groups as registrations complete
- Keep the Insights workbook pinned for the first month to catch gaps quickly
Why is legacy MFA no longer enough?
Legacy MFA (e.g. SMS, OTP apps) can be intercepted by reverse-proxy phishing kits. These kits capture one-time codes and session cookies, allowing attackers to bypass MFA prompts entirely.
Which methods count as phishing-resistant in Entra ID?
FIDO2 security keys / Passkeys
Windows Hello for Business
Certificate-based authentication (CBA)
These methods resist man-in-the-middle and token replay attacks.
What licence do I need?
Microsoft Entra ID P1: Required for Conditional Access targeting users.
Microsoft Entra ID P2: Only needed if using Identity Protection or risk-based policies.
What happens if a user doesn’t have a phishing-resistant method registered?
If enforced, access will be blocked. Use Report-only mode first to identify gaps and helpdesk impact before enforcing.
Can I use this for frontline/shared devices?
Yes. Use QR code authentication for shared device scenarios.
Feel free to buy me a coffee to keep this website up and running
Stop defending yesterday’s attacks with yesterday’s MFA. Require Phishing-resistant MFA for admins and your critical apps, validate outcomes in Insights & Reporting and Sign-in logs, then roll it across the rest of the estate. You’ll cut account-takeover risk, reduce MFA fatigue, and make real-time phishing kits useless against you
Tags: Entra ID