Temporary Access Pass Setup & Custom Banned Passwords In Entra
Temporary Access Pass and custom banned passwords in Microsoft Entra ID
Temporary Access Pass (TAP) and custom banned passwords strengthen sign-in security in Microsoft Entra ID. Used together with Self-Service Password Reset (SSPR) and the My Staff portal, they reduce helpdesk load while enforcing strong password rules. This guide explains what they do, how to set them up, and how they fit with SSPR and delegated resets.
Never miss an article and subscribe
Why use both
- Give users short-term access when they’ve lost a device or are onboarding.
- Stop weak or predictable passwords with a tailored banned list.
- Let managers help staff without over-privileged admin roles.
- Keep a clear audit trail in Entra ID.
Temporary Access Pass – what it is and when to use it
TAP is a short-lived code created by an administrator. It lets a user sign in securely and register or recover their primary methods.
Good uses
- New starters: access while they register MFA.
- Lost device: quick recovery without waiting on support.
- Re-registration: move to a new authenticator or number.
- Contractors: short-term access with strict expiry.
Set up TAP (step-by-step)
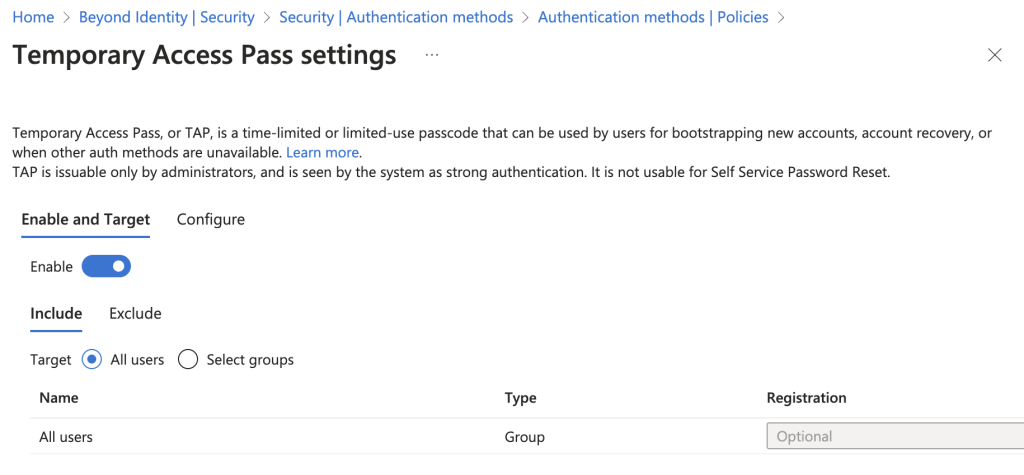
- In entra.microsoft.com, open Protection → Authentication methods → Temporary Access Pass.
- Enable the method and scope it to the right users or groups.
- Set lifetime, length, and whether codes are single-use or multi-use (single-use is safer).
- To issue a code: Users → select user → Authentication methods → Add method → Temporary Access Pass → Add.
- Share the code securely (do not email in plain text).
Tips
- Treat TAP like a password; handle and store it securely.
- Ask the user to add a permanent method (Authenticator app, FIDO2, etc.) straight after sign-in.
- Monitor issued codes in Audit logs.
Custom banned passwords – stop weak choices
A custom banned password list blocks words and patterns specific to your organisation, on top of Microsoft’s global blocklist.
Configure custom banned passwords
- Go to Protection → Authentication methods → Password protection.
- Enable the custom banned list and enter words/phrases (one per line). Include brand names, local slang, team names and predictable patterns.
- Apply the policy to users (and to on-prem AD if you run password protection there).
- Communicate the rules so users know what won’t be accepted.
When this helps
- Regulated industries and public sector.
- Organisations with frequent resets.
- High-profile brands targeted by guessable terms.
Maintenance
- Review and update the list when new risks appear or naming changes.
- Combine with MFA for stronger protection.
Link TAP and custom bans with SSPR and My Staff
Self-Service Password Reset (SSPR)
- Let users reset or unlock without raising a ticket.
- Choose the number/types of factors required.
- With a custom banned list on, weak choices are blocked at reset.
- If a user can’t register SSPR yet, issue a Temporary Access Pass so they can complete registration.
My Staff and Administrative Units
- My Staff lets designated managers reset passwords for their team.
- Administrative Units scope who each manager can help.
- Managers can issue a TAP for urgent access; the banned list still applies during password change.
Operational wins
- Efficiency: managers handle simple cases; IT focuses on exceptions.
- Security: custom bans enforced everywhere a password is set.
- Visibility: central auditing of TAP issuance and password events.
Good practice
- Use single-use TAP where possible and short lifetimes.
- Keep the banned list short, targeted and updated.
- Enforce MFA for everyone.
- Use the least-privileged admin roles; avoid Global Administrator for routine tasks.
- Review Audit logs and Sign-in logs regularly.
FAQs
Can I limit TAP to certain teams?
Yes—scope the authentication method to groups.
How do I share TAP securely?
Use a secure channel (e.g., phone, in-person, or an encrypted message). Avoid plain-text email or chat.
Does the banned list affect SSPR and manager resets?
Yes—the custom list applies wherever a password is set or reset.
Should I allow multi-use TAP?
Only if you have a strong reason. Single-use with short lifetime is safer.
If this article helped feel free to buy me a coffee
Checkout this article Break Glass Accounts in Microsoft 365 How to Stay in Control
Tags: Entra ID